SSL Proxy를 운영하기 위해서는 Root CA로부터 받은 하나의 Site 인증서만으로는 구동되지 않고, SSL Proxy 자체적으로 Root 인증서를 가지고 있으면서 실시간으로 Site 인증서를 만들어야 합니다. SSL Proxy 프로그램을 만들 때 마다 했던 거 또 하고, 했던 거 또 하고... 그런데 기억도 잘 안나고... ㅠㅠ 그래서 SSL Proxy 운영을 위한 Root 인증서를 세팅하고, 실시간으로 Site 인증서를 만드는 과정을 정리해 봤습니다.
OpenSSL 설치
- OpenSSL 사이트( http://slproweb.com/products/Win32OpenSSL.html )에서 자신의 시스템에 맞는 파일( Win64 OpenSSL v1.0.1f )을 설치합니다.
- openssl.exe 실행 파일이 있는 곳을 PATH로 추가해 줍니다.
Root 인증서 만들기
- _ssl_make_root 라는 명령어를 통해서 Root CA 인증서를 만듭니다.
usage : _ssl_make_root <common name>
example : _ssl_make_root VDream
- 예제로 "VDream"을 Common Name으로 하여 Root 인증서를 만들어 보겠습니다.
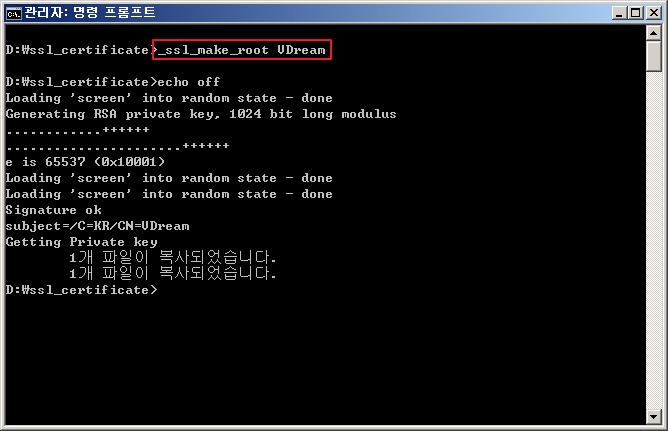
- _make_root 명령어를 통해서 다음과 같은 파일이 생성됩니다.
파일 | 설명 |
root.key ( cakey.pem ) | Root private key file (외부에 공개하면 안됨) |
root.csr | Root certificate request file |
root.crt ( cacert.pem ) | Root cretificate file (외부 공개용 인증서 파일) |
[root.key ( cakey.pem) ]
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDKjwH2z46+3/Xv6SdqJ/oqgmY+OH74nWtTy6LKoC6QMvm/T0ZE
7YGne3UByF3h2aoyjN2Es21keVgieYHgfnIztUgUFR7eWmpRGvwLRihoGYPlrVNo
05Itd7PGAuhILSEKsezjrQQ5aY2wLdOntWxqGpKxo3vm1Q4mBvGYmdQCSQIDAQAB
AoGAUhsXu7i0bvCPWzkSDfi4ceS7lvsFlLcSmzvO9/1oAnF3RLHYlPYE+SOU8S0L
yRGW6LiqzjCA5ho9vHOuTpZSqaOEwMsA77H/ldSo8HR4Rx9T7Vdu+MzWpHpXbPDy
2/I/KmBHqQfpQAvsSlC1V/gsMA59moI5qasRiIZ/6y/u0QECQQD72ViPNzI+2jFb
wznrGImimQO6ibVQWgRvez795aNeCWEgF2lHElQ1NqHb44qIbm+DSMlKMWjlPCNW
IryqQr8hAkEAzeWveEf+kePKtcLJMH/D3vSNK6a6LGNZXsJ5gVhw0VYy5geddffU
+/FPFq9WwosMhLZcB6WZROkr6BvoarSmKQJBAO7Jgtg3Y2KIiqgQkIfBei46mnhx
PQJ0dyQkXPNqmdz9U6OTzvPeAw15QTo1ohH9c6msh33bHzPKM07mHK/qHUECQQC5
7oasiecbe6dcyA/C2j3ZIuIw3xkUaIsWBWyQH3uRrtO74niRRUJyWZFgHOquN78Q
QVWOGj70edQKgNk7MvMxAkBwm07i+E+M0l8eb9RjEvCY/Q9lpZdJCZFd6752kB69
DDfYA1oo9ICUV3l/RV8UJ8+zPLrNt1BRhOeNuux1d3Rf
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE REQUEST-----MIIBXTCBxwIBADAeMQswCQYDVQQGEwJLUjEPMA0GA1UEAwwGVkRyZWFtMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDKjwH2z46+3/Xv6SdqJ/oqgmY+OH74nWtTy6LKoC6QMvm/T0ZE7YGne3UByF3h2aoyjN2Es21keVgieYHgfnIztUgUFR7eWmpRGvwLRihoGYPlrVNo05Itd7PGAuhILSEKsezjrQQ5aY2wLdOntWxqGpKxo3vm1Q4mBvGYmdQCSQIDAQABoAAwDQYJKoZIhvcNAQEFBQADgYEAqUA/4MTdbWnBDZ3MT88dSFzIruiZZE5D/dcAj7zG8Qca+5mu9KJtvvKQ8muI0MYW76NihcySvr/aqIEk83P8NyCIGiLvZXxi7BlVJ+YRgrCztYMvR7CqRQZAZskCczlw9gdSZf4W0G7VeSdobT3TNf3tG1XDNIZK379d6RsBZCY=-----END CERTIFICATE REQUEST-----
-----BEGIN CERTIFICATE-----MIIBszCCARwCCQDKINrDu6w8tjANBgkqhkiG9w0BAQUFADAeMQswCQYDVQQGEwJLUjEPMA0GA1UEAwwGVkRyZWFtMB4XDTE0MDIyNzAxMzUwN1oXDTI0MDIyNTAxMzUwN1owHjELMAkGA1UEBhMCS1IxDzANBgNVBAMMBlZEcmVhbTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAyo8B9s+Ovt/17+knaif6KoJmPjh++J1rU8uiyqAukDL5v09GRO2Bp3t1Achd4dmqMozdhLNtZHlYInmB4H5yM7VIFBUe3lpqURr8C0YoaBmD5a1TaNOSLXezxgLoSC0hCrHs460EOWmNsC3Tp7VsahqSsaN75tUOJgbxmJnUAkkCAwEAATANBgkqhkiG9w0BAQUFAAOBgQBcBYNeDTJedDf27s153aeMcfm4unBJ4dQ4X0Lq/lOVidQC8QxidhKn9T/FSspheLZrppJZWjUWfXiWzFfSMEhfNp+u9d85EY5/OlfiyVhU6MPGPTE/CMK9ZerHnyhFQqvrNWdW0psF89GVXd9cqr1dN2YF8XL/KGBoQKi7OEp32g==-----END CERTIFICATE-----
- root.crt 파일을 더블 클릭하여 인증서 정보를 봅니다. 신뢰할 수 없다는 메세지가 보입니다.
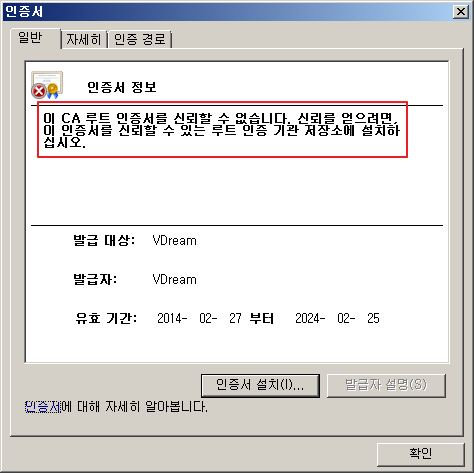
- 다음과 같은 절차를 통해 root.crt 파일을 신뢰할 수 있는 루트 인증 기관에 설치를 합니다.
root.crt 파일 더블클릭 > 인증서 설치 > "모든 인증서를 다음 저장소에 저장" > "신뢰할 수 있는 루트 인증 기관"
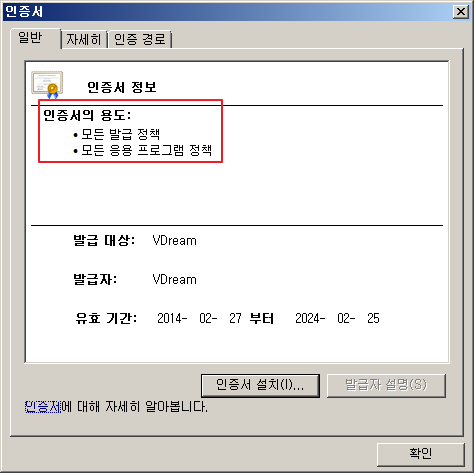
- 인증서 설치가 완료되고 난 뒤 인증서 보기를 하면 다음과 같이 정상적인 Root 인증서로 나타 납니다.
- SSL Proxy를 운영할 때에는 실시간으로 Site 인증서를 만들어야 합니다. Site 인증서는 다음과 같은 명령어로 만듭니다.
usage : _ssl_make_site <common name>example : _ssl_make_site test.com
- 예제로 Common Name을 "test.com"로 인증서를 만들어 보겠습니다.
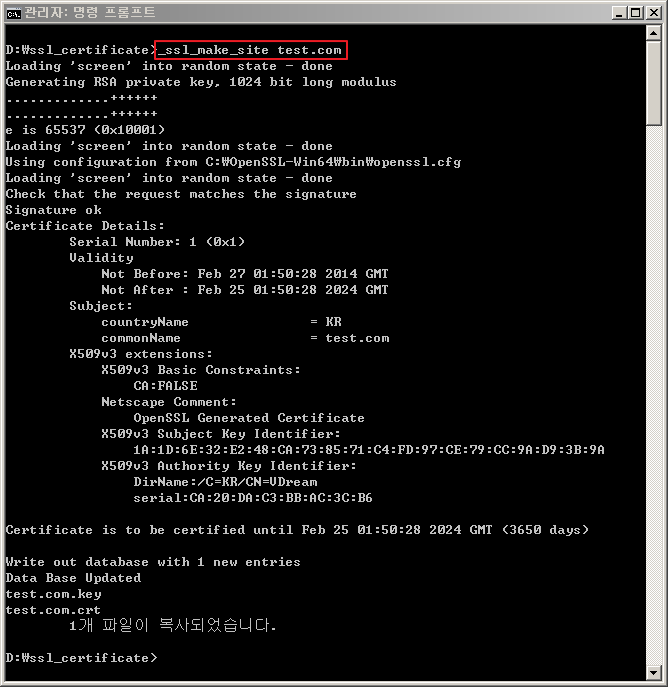
- 다음과 같은 파일이 생성됩니다. SSL Proxy(혹은 SSL Web Server)는 key와 crt 정보가 같이 있는 test.com.pem 파일을 이용하여 서버를 구동시키면 됩니다.
파일 | 설명 |
test.com.key | Site private key file (외부에 공개하면 안됨) |
test.com.csr | Site certificate request file |
test.com.crt | Site certificate file (외부 공개용 인증서 파일) |
test.com.pem | key + crt file (SSL 서버 운영을 위한 파일) |
-----BEGIN RSA PRIVATE KEY-----MIICXAIBAAKBgQDZRlgLA+YKJm3oKRKXWY88HaNSLuJuoMyS2SFGCpVBD7WT1oI/ncU6E+vznceZH4oa/na0xFmWRurHuDhYuTf94iwZkhlxWVDIS/q8Lb48wA6lgp36XDZZYyQK+wMfuUAqwExJLclt9wo6DFaRn9RCCvjHgkJhThKsa3KTCHASOwIDAQABAoGASvqTd3mo8OfCFdPWrpQhccVojvvO+A5VineTm/AbAZDCQHpOCFYRsbEeQ7u3HYhcyGP34vm/ULS4YKOaDkQcpcVTQC6bd0d1h35J8HRJu8RhFVCvFYAaLYHyxUWWGjNGx4i3DsFlWFzDeRHjiLN2/bfEVh4fLp+6GumlWRlc/cECQQD51axmZJlelBuGZppoFQxdqpjTE/ephHBEmh7aDwbcYE9VrLF9nJW4L/kbPciCI/iD6j7Hj52o/ayhEA811yY9AkEA3qL5VFMRW8IHjjusbrP25y49kMqBqnVD/XufmvvjJdnZP7dS85euHQgwlMTPvONwBxQsJ2Ux9CDsMCqFST8Z1wJBANz7ErK+6Kmvd2k59/l4JKf07ZhGYRmf+22ypPdbs0XaKlItnhDtH8D7LevaijASgQ6tczow3dNMDhWojsugskECQGATwLlNJ76LWytcQSt86l4VrGfhnFdtR6wKP3RoozvgaUp/2IJawL6ynBR3YpbHJ79GS0+s8gPCeWrHzsEvQ/0CQBoV9mPgU2LBih7Is8YkgFfPNtem9hMEA6dO7isvxP3u8YYPxuwL99qdwIGfzNANMtjVLdkkpnfYM1Pm3u1uJqU=-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE REQUEST-----MIIBXzCByQIBADAgMQswCQYDVQQGEwJLUjERMA8GA1UEAwwIdGVzdC5jb20wgZ8wDQYJKoZIhvcNAQEBBQADgY0AMIGJAoGBANlGWAsD5gombegpEpdZjzwdo1Iu4m6gzJLZIUYKlUEPtZPWgj+dxToT6/Odx5kfihr+drTEWZZG6se4OFi5N/3iLBmSGXFZUMhL+rwtvjzADqWCnfpcNlljJAr7Ax+5QCrATEktyW33CjoMVpGf1EIK+MeCQmFOEqxrcpMIcBI7AgMBAAGgADANBgkqhkiG9w0BAQUFAAOBgQAWepkQjgRCNC6jxEo4JIKEcMCbZMj0AlJx+l0QgB+k9xtPlsES0+MR62A1wt2/pnctX28UbUwpeiopaZV9h+Ez5W6eqqmK1ZG0vo0fXpe8br2hIPdwzq2bgzDrCeXbsSylBX79z0DuLDn+9l7lcbE6MoDQr105nPG8ZpGafQDazg==-----END CERTIFICATE REQUEST-----
Certificate:Data:Version: 3 (0x2)Serial Number: 1 (0x1)Signature Algorithm: sha1WithRSAEncryptionIssuer: C=KR, CN=VDreamValidityNot Before: Feb 27 01:50:28 2014 GMTNot After : Feb 25 01:50:28 2024 GMTSubject: C=KR, CN=test.comSubject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (1024 bit)Modulus:00:d9:46:58:0b:03:e6:0a:26:6d:e8:29:12:97:59:8f:3c:1d:a3:52:2e:e2:6e:a0:cc:92:d9:21:46:0a:95:41:0f:b5:93:d6:82:3f:9d:c5:3a:13:eb:f3:9d:c7:99:1f:8a:1a:fe:76:b4:c4:59:96:46:ea:c7:b8:38:58:b9:37:fd:e2:2c:19:92:19:71:59:50:c8:4b:fa:bc:2d:be:3c:c0:0e:a5:82:9d:fa:5c:36:59:63:24:0a:fb:03:1f:b9:40:2a:c0:4c:49:2d:c9:6d:f7:0a:3a:0c:56:91:9f:d4:42:0a:f8:c7:82:42:61:4e:12:ac:6b:72:93:08:70:12:3bExponent: 65537 (0x10001)X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:1A:1D:6E:32:E2:48:CA:73:85:71:C4:FD:97:CE:79:CC:9A:D9:3B:9AX509v3 Authority Key Identifier:DirName:/C=KR/CN=VDreamserial:CA:20:DA:C3:BB:AC:3C:B6Signature Algorithm: sha1WithRSAEncryption70:77:f2:b2:62:bb:e8:9b:81:54:a4:9a:d4:4b:11:65:f9:85:92:35:68:68:07:64:cd:10:ee:85:c3:ff:ff:26:cd:fd:93:04:37:72:e5:dc:3c:08:38:a1:24:95:48:e1:e2:5a:d0:52:36:17:d3:41:d6:c5:d2:83:06:60:7b:c9:83:d7:cc:c1:68:61:f6:cc:ea:99:68:60:b8:ab:ef:24:ed:9d:d5:33:4a:75:9a:13:7c:07:bc:4a:55:99:c5:ea:25:f9:47:2f:8f:76:d2:3c:2a:fa:25:0d:c5:7b:3d:34:6e:16:44:16:c1:94:6c:83:a6:75:b0:26:28:d5:6c:d4-----BEGIN CERTIFICATE-----MIICSjCCAbOgAwIBAgIBATANBgkqhkiG9w0BAQUFADAeMQswCQYDVQQGEwJLUjEPMA0GA1UEAwwGVkRyZWFtMB4XDTE0MDIyNzAxNTAyOFoXDTI0MDIyNTAxNTAyOFowIDELMAkGA1UEBhMCS1IxETAPBgNVBAMMCHRlc3QuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDZRlgLA+YKJm3oKRKXWY88HaNSLuJuoMyS2SFGCpVBD7WT1oI/ncU6E+vznceZH4oa/na0xFmWRurHuDhYuTf94iwZkhlxWVDIS/q8Lb48wA6lgp36XDZZYyQK+wMfuUAqwExJLclt9wo6DFaRn9RCCvjHgkJhThKsa3KTCHASOwIDAQABo4GVMIGSMAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBQaHW4y4kjKc4VxxP2XznnMmtk7mjA4BgNVHSMEMTAvoSKkIDAeMQswCQYDVQQGEwJLUjEPMA0GA1UEAwwGVkRyZWFtggkAyiDaw7usPLYwDQYJKoZIhvcNAQEFBQADgYEAcHfysmK76JuBVKSa1EsRZfmFkjVoaAdkzRDuhcP//ybN/ZMEN3Ll3DwIOKEklUjh4lrQUjYX00HWxdKDBmB7yYPXzMFoYfbM6ploYLir7yTtndUzSnWaE3wHvEpVmcXqJflHL4920jwq+iUNxXs9NG4WRBbBlGyDpnWwJijVbNQ=-----END CERTIFICATE-----
-----BEGIN RSA PRIVATE KEY-----MIICXAIBAAKBgQDZRlgLA+YKJm3oKRKXWY88HaNSLuJuoMyS2SFGCpVBD7WT1oI/ncU6E+vznceZH4oa/na0xFmWRurHuDhYuTf94iwZkhlxWVDIS/q8Lb48wA6lgp36XDZZYyQK+wMfuUAqwExJLclt9wo6DFaRn9RCCvjHgkJhThKsa3KTCHASOwIDAQABAoGASvqTd3mo8OfCFdPWrpQhccVojvvO+A5VineTm/AbAZDCQHpOCFYRsbEeQ7u3HYhcyGP34vm/ULS4YKOaDkQcpcVTQC6bd0d1h35J8HRJu8RhFVCvFYAaLYHyxUWWGjNGx4i3DsFlWFzDeRHjiLN2/bfEVh4fLp+6GumlWRlc/cECQQD51axmZJlelBuGZppoFQxdqpjTE/ephHBEmh7aDwbcYE9VrLF9nJW4L/kbPciCI/iD6j7Hj52o/ayhEA811yY9AkEA3qL5VFMRW8IHjjusbrP25y49kMqBqnVD/XufmvvjJdnZP7dS85euHQgwlMTPvONwBxQsJ2Ux9CDsMCqFST8Z1wJBANz7ErK+6Kmvd2k59/l4JKf07ZhGYRmf+22ypPdbs0XaKlItnhDtH8D7LevaijASgQ6tczow3dNMDhWojsugskECQGATwLlNJ76LWytcQSt86l4VrGfhnFdtR6wKP3RoozvgaUp/2IJawL6ynBR3YpbHJ79GS0+s8gPCeWrHzsEvQ/0CQBoV9mPgU2LBih7Is8YkgFfPNtem9hMEA6dO7isvxP3u8YYPxuwL99qdwIGfzNANMtjVLdkkpnfYM1Pm3u1uJqU=-----END RSA PRIVATE KEY-----Certificate:Data:Version: 3 (0x2)Serial Number: 1 (0x1)Signature Algorithm: sha1WithRSAEncryptionIssuer: C=KR, CN=VDreamValidityNot Before: Feb 27 01:50:28 2014 GMTNot After : Feb 25 01:50:28 2024 GMTSubject: C=KR, CN=test.comSubject Public Key Info:Public Key Algorithm: rsaEncryptionPublic-Key: (1024 bit)Modulus:00:d9:46:58:0b:03:e6:0a:26:6d:e8:29:12:97:59:8f:3c:1d:a3:52:2e:e2:6e:a0:cc:92:d9:21:46:0a:95:41:0f:b5:93:d6:82:3f:9d:c5:3a:13:eb:f3:9d:c7:99:1f:8a:1a:fe:76:b4:c4:59:96:46:ea:c7:b8:38:58:b9:37:fd:e2:2c:19:92:19:71:59:50:c8:4b:fa:bc:2d:be:3c:c0:0e:a5:82:9d:fa:5c:36:59:63:24:0a:fb:03:1f:b9:40:2a:c0:4c:49:2d:c9:6d:f7:0a:3a:0c:56:91:9f:d4:42:0a:f8:c7:82:42:61:4e:12:ac:6b:72:93:08:70:12:3bExponent: 65537 (0x10001)X509v3 extensions:X509v3 Basic Constraints:CA:FALSENetscape Comment:OpenSSL Generated CertificateX509v3 Subject Key Identifier:1A:1D:6E:32:E2:48:CA:73:85:71:C4:FD:97:CE:79:CC:9A:D9:3B:9AX509v3 Authority Key Identifier:DirName:/C=KR/CN=VDreamserial:CA:20:DA:C3:BB:AC:3C:B6Signature Algorithm: sha1WithRSAEncryption70:77:f2:b2:62:bb:e8:9b:81:54:a4:9a:d4:4b:11:65:f9:85:92:35:68:68:07:64:cd:10:ee:85:c3:ff:ff:26:cd:fd:93:04:37:72:e5:dc:3c:08:38:a1:24:95:48:e1:e2:5a:d0:52:36:17:d3:41:d6:c5:d2:83:06:60:7b:c9:83:d7:cc:c1:68:61:f6:cc:ea:99:68:60:b8:ab:ef:24:ed:9d:d5:33:4a:75:9a:13:7c:07:bc:4a:55:99:c5:ea:25:f9:47:2f:8f:76:d2:3c:2a:fa:25:0d:c5:7b:3d:34:6e:16:44:16:c1:94:6c:83:a6:75:b0:26:28:d5:6c:d4-----BEGIN CERTIFICATE-----MIICSjCCAbOgAwIBAgIBATANBgkqhkiG9w0BAQUFADAeMQswCQYDVQQGEwJLUjEPMA0GA1UEAwwGVkRyZWFtMB4XDTE0MDIyNzAxNTAyOFoXDTI0MDIyNTAxNTAyOFowIDELMAkGA1UEBhMCS1IxETAPBgNVBAMMCHRlc3QuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDZRlgLA+YKJm3oKRKXWY88HaNSLuJuoMyS2SFGCpVBD7WT1oI/ncU6E+vznceZH4oa/na0xFmWRurHuDhYuTf94iwZkhlxWVDIS/q8Lb48wA6lgp36XDZZYyQK+wMfuUAqwExJLclt9wo6DFaRn9RCCvjHgkJhThKsa3KTCHASOwIDAQABo4GVMIGSMAkGA1UdEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBQaHW4y4kjKc4VxxP2XznnMmtk7mjA4BgNVHSMEMTAvoSKkIDAeMQswCQYDVQQGEwJLUjEPMA0GA1UEAwwGVkRyZWFtggkAyiDaw7usPLYwDQYJKoZIhvcNAQEFBQADgYEAcHfysmK76JuBVKSa1EsRZfmFkjVoaAdkzRDuhcP//ybN/ZMEN3Ll3DwIOKEklUjh4lrQUjYX00HWxdKDBmB7yYPXzMFoYfbM6ploYLir7yTtndUzSnWaE3wHvEpVmcXqJflHL4920jwq+iUNxXs9NG4WRBbBlGyDpnWwJijVbNQ=-----END CERTIFICATE-----

